模糊测试(一)——AFL++调研记录
What is Fuzz Testing?
Fuzz Testing is a software testing technique that employs automatically generated random inputs to identify potential vulnerabilities in software.
Fuzz Testing Process
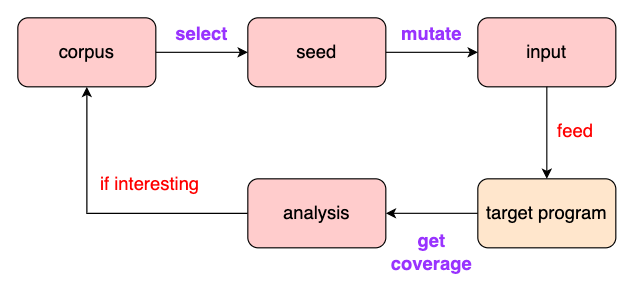
The fuzz testing process, illustrated in the Figure below, which can be divided into seed selection, input mutation and result analysis.
Important Sub-processes
Instrumentation
Instrumentation adds hooks to the target program to collect runtime information while preserving the original behavior of the program.
The methods for instrumentation differ depending on whether the source code is available.
- Source code available:
- A basic method is inserting debugging statements such as
print()or logging functions. Although this method is simple and direct, it is labor-intensive and error-prone. - Modern compilers provide the ability to insert instrumentation automatically. GCC/Clang automatically insert instrumentation code using flags like
-finstrument=functions.
- A basic method is inserting debugging statements such as
- Source code not available:
- Static binary rewriting involves modifying the executable file on disk before it is run.
- Dynamic binary instrumentation (DBI) tools insert instrumentation code in memory at runtime, which is the most common and powerful approach for binary software.
Sanitizer
Sanitizers are typical tools of compiler-based instrumentation including Address Sanitizer(ASan), Memory Sanitizer(MSan), Undefined Behavior Sanitizer(UBSan), and Thread Sanitizer(TSan).
Code can be compiled with sanitizers by adding flags such as -fsanitize=address or -fsanitize=memory, which instruct the compiler to insert runtime checks into the program.
AFL++
AFL++ is born from AFL and incorporates various improvements and extensions.